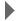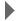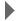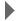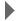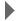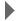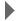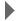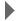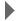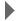The approach below still works, but there is an update to this question for newer versions of Ivy on our new community page:
[https://community.axonivy.com/d/58-how-to-migrate-active-directory-connection-to-ldaps-ssl][1]
The generic approach that should work in any ivyEngine:
**1. Set the SSL Debug flag**
Set the JVM system property `-Djavax.net.debug=all` to debug SSL connections . https://docs.oracle.com/javase/7/docs/technotes/guides/security/jsse/ReadDebug.html
* ivy8: use the `configuration/jvm.options` file to set the JVM property:
https://dev.axonivy.com/doc/8.0/engine-guide/configuration/files/jvm-options.html?highlight=jvm%20options
* ivy7 and older: setup a `configuration/*.ILC` file that matches your binary being used to start the engine.
https://dev.axonivy.com/doc/7.0/EngineGuideHtml/misc.html#misc-toolreference-ilc
* 7.0 ILC example: sets the JMV property for the 'AxonIvyEngineC.exe' (other binaries will not have the property set) ![alt text][2]
**2. Determine the truststore in use**
The truststore that contains the accepted certificats of your engine runtime must be identified. The location differs according to your operating system and ivyEngine version (JVM version). Analyse the Axon.ivy console log and find the log entry exposing your 'truststore' . E.g. ( `jre/lib/security/cacerts` or `jre/lib/security/jssecacerty` )
![alt text][3]
**3. Add Certificates to Truststore**
Add all parent certificates of your LDAP(S) server to the truststore using the `keytool` availalbe in the JRE/lib/bin of the engine being used. Sample:
`jre/lib/bin/keytool -importcert -file zugtstdirads.cer -keystore jre/lib/security/cacerts -storepass changeit -alias zugtstdirads`
You may use a GUI such as [https://keystore-explorer.org/][4] to verify that certificates have been propertly added. But that should just be used for verification. Adding certificates with this tooling may lead to corrupt truststores (and the engine/HTTPS connctor no longer starts correctly).
3.2 Verify, that the issuer of your certificate is in the truststore. In most cases you have to add internal company CA certs that will finally link to a ROOT CA Issuer.
![alt text][5]
**4. Enable SSL connections**
... for your Active Directory security system
- ivy8: Engine Cockpit -> Security Systems -> YourAd -> Enable 'SSL' + and adjust the URL port (636)
- ivy 7 an older: Admin UI -> Your App -> Edit Active Directory -> Enable 'SSL' with the checkbox.
![alt text][6]
**5. Trigger the synchronization**
If the connection is not working: check the Axon.ivy console.log for SSL debug output. In most cases a certificate in the chain is missing.
As a first step: Verify that your added certificates appear in the list of trusted certs:
![alt text][7]
See point 3.2 to analyze the cert-chain.
**NOTE:** At the end, do not forget tor remove the `-Djavax.net.debug=all` entry from the configuration file once everything is OK, and then to restart the engine, otherwise you will encounter performance problems.
[1]: https://community.axonivy.com/d/58-how-to-migrate-active-directory-connection-to-ldaps-ssl
[2]: https://answers.axonivy.com/upfiles/ilcExampleDebugProperty.png
[3]: https://answers.axonivy.com/upfiles/identifySSLtruststore.png
[4]: https://keystore-explorer.org/
[5]: https://answers.axonivy.com/upfiles/keystore-explorer_truststoreWithCertAndCaIssuer.png
[6]: https://answers.axonivy.com/upfiles/cockpitUseSSL.png
[7]: https://answers.axonivy.com/upfiles/debugCertAdding.png